Server security for IoT devices: protecting your connected devices – Yo, ever thought about how vulnerable your smart home gadgets […]
Tag: server security
Secure Remote Access: Protecting Your Servers with Strong Connections and Authentication
Server security for remote access: secure connections and authentication – Secure remote access: secure connections and authentication – this is […]
Server Security Vulnerabilities: Common Threats and Mitigation Strategies
Server security vulnerabilities: common threats and mitigation strategies sets the stage for this enthralling narrative, offering readers a glimpse into […]
Server Security Best Practices: Hardening Systems, Protecting Data
Server security best practices: hardening your system and protecting your data are crucial for any organization that relies on digital […]
Secure Your Servers: Monitoring, Logging, and Threat Response
In the ever-evolving digital landscape, securing your servers is paramount. Server security monitoring and logging: detecting and responding to threats, […]
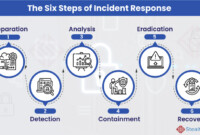
Server Security Incident Response: Steps for a Breach
Server security incident response plan: steps to take in case of a breach – Server security incident response plans are […]
Securing Cloud Applications: Best Practices and Considerations
In the ever-evolving landscape of cloud computing, safeguarding sensitive data and applications has become paramount. ‘Server security for cloud-based applications: […]
Dedicated Server Security: Essential Steps and Tools
Dedicated server security: essential steps and tools are paramount in today’s digital landscape, where cyber threats are constantly evolving. While […]
Secure Your Dedicated Server: Defending Against Hackers and Malware
How to secure a dedicated server from hackers and malware is a critical concern for anyone running a website or […]
Dedicated Gaming Servers: Choosing the Right Hardware and Software
Dedicated server for gaming: choosing the right hardware and software sets the stage for a smooth and immersive gaming experience. […]