In the ever-evolving digital landscape, securing your servers is paramount. Server security monitoring and logging: detecting and responding to threats, forms the cornerstone of a robust defense strategy. Imagine a fortress, meticulously guarded with watchful eyes and a detailed log of every visitor and activity.
This is the essence of server security – vigilance and documentation. Each log entry becomes a piece of evidence, helping us understand what happened, why it happened, and how to prevent it from happening again. This proactive approach not only safeguards our data but also ensures compliance with regulations and builds trust with our users.
This exploration will delve into the intricacies of server security monitoring and logging, covering essential components, threat detection techniques, incident response strategies, and best practices. We will uncover the power of anomaly detection algorithms, the importance of centralized logging, and the role of automation in thwarting threats.
We will also examine the future of server security, exploring the impact of emerging technologies like artificial intelligence and cloud computing.
Key Components of Server Security Monitoring and Logging: Server Security Monitoring And Logging: Detecting And Responding To Threats

A robust server security monitoring and logging system is the backbone of any organization’s security posture. It provides the essential tools and insights to detect, investigate, and respond to potential threats. This system involves various key components working together to achieve a comprehensive view of server activity and security events.
Types of Logs, Server security monitoring and logging: detecting and responding to threats
Server logs are invaluable records that document the activities and events occurring on a server. These logs serve as a historical record of actions, errors, and security events, providing crucial information for troubleshooting, security analysis, and incident response.
- System Logs:These logs capture critical system events, such as boot processes, software installations, user logins, and system errors. System logs provide a comprehensive overview of the server’s operational health and potential security breaches.
- Application Logs:Application logs track the activities and events within specific applications running on the server. These logs can reveal application errors, user interactions, and potential vulnerabilities, providing insights into application performance and security issues.
- Security Logs:Security logs are dedicated to recording security-related events, such as failed login attempts, file access attempts, and security policy violations. These logs are crucial for identifying and investigating potential security threats.
- Web Server Logs:Web server logs track website access, user requests, and website errors. They provide valuable information about website traffic, user behavior, and potential security vulnerabilities.
- Firewall Logs:Firewall logs record network traffic that passes through the firewall, including blocked connections, allowed connections, and potential security threats. These logs are essential for understanding network security and identifying suspicious network activity.
Centralized Logging and Log Management
Centralized logging consolidates logs from multiple servers into a single location, simplifying log analysis and providing a unified view of security events across the entire network. Log management solutions enhance centralized logging by providing tools for log aggregation, analysis, correlation, and reporting.
- Simplified Log Analysis:Centralized logging allows security analysts to easily search, filter, and analyze logs from multiple servers in a single location, improving efficiency and effectiveness.
- Enhanced Security Monitoring:By aggregating logs from various sources, centralized logging enables organizations to gain a comprehensive view of security events across their entire infrastructure, facilitating early detection of threats.
- Improved Incident Response:Centralized logging provides a centralized repository of security events, making it easier to investigate security incidents, identify the root cause, and implement corrective actions.
- Compliance and Auditing:Centralized logging solutions facilitate compliance with industry regulations and security standards by providing a comprehensive record of security events for auditing purposes.
Techniques for Detecting Threats

Detecting threats in server security monitoring is like being a detective in a digital world. You need to find the clues and patterns that point to malicious activity, and then use your knowledge to understand the motives and methods behind the attacks.
This involves using a combination of tools and techniques, with anomaly detection algorithms and log analysis being some of the most effective.
Anomaly Detection Algorithms
Anomaly detection algorithms play a crucial role in identifying unusual patterns in server activity that could signal a threat. They work by establishing a baseline of normal behavior and then flagging any deviations from this baseline as potential threats. These algorithms are like vigilant security guards, always watching for any suspicious activity that might be out of the ordinary.There are various types of anomaly detection algorithms, each with its own strengths and weaknesses.
Here are some common approaches:
- Statistical Methods:These algorithms use statistical techniques to identify outliers in data. For example, they might look for events that occur with a frequency significantly different from the average. This is like noticing that someone is spending an unusually long time browsing a particular website, which could be a sign of malicious activity.
- Machine Learning:Machine learning algorithms can be trained on historical data to identify patterns that indicate normal behavior. They can then use this knowledge to detect anomalies in real-time. This is like teaching a machine to recognize the typical patterns of a person’s walking gait, and then alerting you if it notices any unusual changes.
- Clustering:Clustering algorithms group similar data points together. Anomalies are then identified as data points that do not belong to any of the established clusters. This is like noticing a group of people walking together in a certain direction, and then identifying someone who is walking alone in the opposite direction, which could be suspicious.
Log Analysis
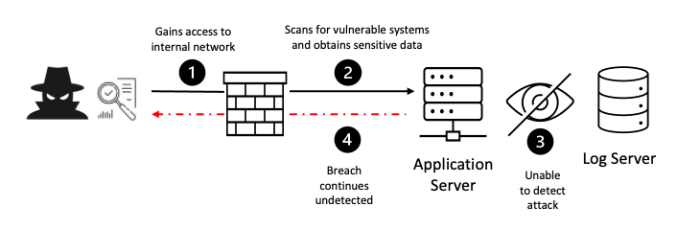
Log analysis is another critical technique for detecting threats. Server logs are like a record of everything that happens on a server, providing valuable insights into potential attacks. By analyzing these logs, security analysts can identify suspicious activities, such as unauthorized access attempts, failed logins, or unusual file modifications.
Proactive server security monitoring and logging are essential for detecting and responding to threats. This includes setting up robust logging systems, implementing intrusion detection and prevention systems, and regularly reviewing security logs. For further guidance on optimizing server security, it’s beneficial to consult resources on Dedicated server management: best practices and tips.
By combining effective security monitoring and best management practices, you can significantly enhance the overall security posture of your servers.
- Identifying Suspicious Activities:Log analysis involves searching for specific patterns and s that indicate malicious activity. For example, looking for repeated failed login attempts from the same IP address could suggest a brute-force attack. Also, searching for unusual file modifications, especially in sensitive directories, could point to data exfiltration or malware installation.
Server security monitoring and logging are crucial for identifying and responding to threats, especially when dealing with dedicated servers. Implementing robust security measures, such as those outlined in Dedicated server security: essential steps and tools , can help you stay ahead of potential attacks.
By continuously monitoring logs and analyzing security events, you can detect suspicious activity, prevent data breaches, and maintain the integrity of your dedicated server.
- Correlation and Context:It’s important to analyze logs in context and correlate events across different logs. For instance, a single failed login attempt might not be suspicious, but if it’s followed by multiple other attempts from the same IP address, it could indicate a coordinated attack.
This is like piecing together clues from different sources to build a complete picture of the crime.
- Using Tools:Log analysis can be done manually, but it’s often more efficient and effective to use specialized tools. These tools can help you filter, search, and analyze logs quickly and efficiently, saving you valuable time and effort.
Common Attack Patterns and Detection Methods
Attackers often employ specific patterns and techniques to compromise servers. Understanding these patterns can help you develop effective detection methods.
- Brute-Force Attacks:These attacks involve repeatedly trying different passwords to gain unauthorized access. You can detect brute-force attacks by monitoring failed login attempts and looking for patterns, such as multiple attempts from the same IP address in a short period of time.
Server security monitoring and logging are essential for detecting and responding to threats. A robust security posture is crucial, especially for high-traffic WordPress websites, which often become targets for malicious attacks. Choosing the right cloud hosting provider, like those listed in this comprehensive guide on Best cloud hosting for WordPress websites with high traffic , can greatly enhance your security.
By utilizing a secure hosting platform, you can leverage their expertise in managing security threats and ensure the safety and integrity of your valuable data.
Implement rate limiting to prevent excessive login attempts. This is like setting a limit on the number of times someone can try to open a door before it locks itself, making it harder for someone to force their way in.
- SQL Injection Attacks:These attacks exploit vulnerabilities in web applications to gain unauthorized access to databases. You can detect SQL injection attacks by monitoring for unusual SQL queries, especially those that contain suspicious characters or s. Use input validation and parameterized queries to prevent SQL injection attacks.
This is like carefully checking someone’s identification before allowing them to enter a restricted area, preventing unauthorized access to sensitive information.
- Cross-Site Scripting (XSS) Attacks:These attacks inject malicious scripts into websites to steal user data or hijack sessions. You can detect XSS attacks by monitoring for unusual HTML code, especially in user-submitted content. Use input validation and output encoding to prevent XSS attacks.
This is like carefully inspecting someone’s luggage before allowing them to board a plane, preventing them from smuggling in harmful objects.
Responding to Security Threats
Detecting threats is only half the battle. Once you’ve identified a security incident, you need to respond quickly and effectively to minimize damage and restore your systems to a secure state. This is where a well-defined incident response plan comes in handy, acting as your roadmap to navigate the chaos.
Incident Response Plans
An incident response plan Artikels the steps to take when a security incident occurs. It’s your playbook for handling everything from data breaches to malware infections. A good plan should include the following elements:
- Identification and Analysis: This involves recognizing the incident, gathering evidence, and understanding the scope and impact of the threat.
- Containment: Here, you isolate the affected systems or networks to prevent further damage and limit the spread of the threat.
- Eradication: This step involves removing the threat, whether it’s malware, unauthorized access, or compromised data.
- Recovery: You restore affected systems and data to their pre-incident state, ensuring that operations can resume normally.
- Lessons Learned: This crucial stage involves reviewing the incident to identify weaknesses in your security posture and implement improvements to prevent similar incidents in the future.
Automation and Orchestration
Responding to security incidents can be a complex and time-consuming process. Automation and orchestration tools can streamline this process by automating repetitive tasks and coordinating actions across different security tools. For example, an automated response system can:
- Trigger alerts: When a security threat is detected, the system can automatically send notifications to the appropriate teams.
- Isolate infected systems: The system can automatically quarantine infected systems to prevent further spread.
- Run remediation scripts: The system can automatically execute scripts to remove malware or restore compromised systems.
Automation and orchestration are like having a team of tireless, efficient robots working 24/7 to protect your systems.
Server security monitoring and logging are crucial for detecting and responding to threats. A robust security posture is especially important for gaming servers, which are often targeted by malicious actors. To ensure the best possible performance and reliability for your gaming server, consider cloud hosting , which offers scalability and resilience.
By implementing strong security measures and leveraging cloud hosting solutions, you can provide a safe and enjoyable gaming experience for your players.
Automation can also help you:
- Improve response time: Automated responses can significantly reduce the time it takes to detect and contain threats, minimizing potential damage.
- Reduce human error: Automation can eliminate the risk of human error in critical tasks, ensuring consistent and reliable responses.
- Scale your security operations: Automation allows you to handle a larger volume of incidents without increasing your staff size.
Best Practices for Server Security Monitoring and Logging
Securing your server is a constant battle against a barrage of cyber threats, and it’s vital to have a robust security monitoring and logging system in place. Like a detective solving a crime, you need the right tools and techniques to gather evidence, analyze the situation, and take swift action.
This section will explore best practices for configuring and managing server security monitoring tools, optimizing log retention and data management, and ensuring the integrity and security of your logging systems.
Configuring and Managing Server Security Monitoring Tools
Effective configuration and management of server security monitoring tools are essential for maximizing their effectiveness.
- Choose the Right Tools:Select tools that meet your specific needs, considering factors like the size and complexity of your infrastructure, the types of threats you face, and your budget. A good analogy is choosing the right tools for a specific task: a carpenter wouldn’t use a hammer to drive screws, just as you wouldn’t use a basic intrusion detection system for advanced threat analysis.
- Centralized Management:Centralize management of your monitoring tools for efficiency and ease of administration. Imagine trying to manage a sprawling network of servers with individual monitoring systems – it’s a recipe for chaos! Centralization allows you to see the big picture and respond to threats more effectively.
Server security monitoring and logging are crucial for detecting and responding to threats, especially for dedicated servers. A robust security strategy includes implementing firewalls, securing network connections, and regularly updating software. To learn more about protecting your dedicated server from hackers and malware, check out this comprehensive guide: How to secure a dedicated server from hackers and malware.
By understanding these best practices and utilizing effective monitoring tools, you can significantly reduce the risk of attacks and ensure the integrity of your server environment.
- Real-time Monitoring:Enable real-time monitoring to detect threats as they occur. Think of it like having a security guard constantly patrolling your server, ready to spot any suspicious activity.
- Alerting and Notifications:Configure alerts and notifications to be triggered when suspicious events occur. This ensures you are notified immediately and can take action before the situation escalates. It’s like having a loud alarm that goes off when an intruder is detected, giving you a chance to respond.
- Regular Updates:Keep your monitoring tools up-to-date with the latest security patches and updates. This is crucial to protect against emerging threats and vulnerabilities. Think of it like giving your security guard the latest training and equipment to stay ahead of the game.
Effective Log Retention and Data Management
Log retention and data management are crucial for successful security monitoring and incident response.
- Log Retention Policy:Establish a clear log retention policy, balancing security requirements with storage constraints. You need enough logs to investigate past incidents, but you don’t want to hoard data indefinitely. Think of it like keeping a well-organized filing system for your server’s history, ensuring you have the right information when needed.
- Log Aggregation:Use log aggregation tools to consolidate logs from multiple servers into a central location for easier analysis. This is like having a single, comprehensive crime scene report instead of scattered evidence.
- Log Analysis and Correlation:Implement tools and techniques for analyzing and correlating logs to identify patterns and potential threats. Think of it like using forensic techniques to connect the dots and uncover the bigger picture.
- Data Encryption:Encrypt log data in transit and at rest to protect it from unauthorized access. This is like locking your server’s evidence room to keep it secure.
Ensuring the Integrity and Security of Logging Systems
Maintaining the integrity and security of your logging systems is essential for trust and reliability.
- Log Integrity Monitoring:Implement mechanisms to monitor the integrity of your logging systems, ensuring that logs are not tampered with or altered. This is like ensuring that the evidence in your server’s crime scene is not compromised.
- Secure Log Storage:Store logs in a secure location, protected from unauthorized access. This is like keeping your server’s evidence in a secure vault.
- Access Control:Implement strict access controls to limit access to log data to authorized personnel. This is like ensuring that only qualified investigators have access to the evidence.
- Regular Auditing:Regularly audit your logging systems to identify and address any security vulnerabilities. This is like periodically inspecting your server’s security measures to ensure they are still effective.
The Future of Server Security Monitoring and Logging

The world of server security monitoring and logging is constantly evolving, driven by the relentless march of technology and the ever-increasing sophistication of cyber threats. The future holds exciting possibilities, with new technologies and approaches poised to revolutionize how we protect our digital assets.
The Rise of Artificial Intelligence and Machine Learning
Artificial intelligence (AI) and machine learning (ML) are rapidly transforming the landscape of server security. These technologies are capable of analyzing vast amounts of data, identifying patterns and anomalies that would be impossible for humans to detect. AI and ML algorithms can learn from past attacks and security incidents, enabling them to proactively identify and respond to new threats.
They can also automate tasks such as threat detection, incident response, and security policy enforcement, freeing up security teams to focus on more strategic initiatives.
- Automated Threat Detection:AI-powered systems can continuously monitor network traffic, system logs, and other data sources for suspicious activity. They can analyze patterns and identify potential threats that might otherwise go unnoticed.
- Anomaly Detection:AI algorithms can detect deviations from normal behavior patterns, such as unusual login attempts, unexpected file accesses, or spikes in network traffic. These anomalies can be early indicators of malicious activity.
- Real-Time Threat Intelligence:AI systems can leverage real-time threat intelligence feeds to stay ahead of emerging threats. They can correlate data from various sources to identify potential attacks before they occur.
- Adaptive Security:AI and ML can help security teams build adaptive security systems that can learn and evolve over time. These systems can automatically adjust security policies based on new threats and vulnerabilities.
Closing Notes
As we navigate the digital age, safeguarding our servers is no longer a luxury but a necessity. By embracing server security monitoring and logging, we empower ourselves with the knowledge and tools to detect, respond to, and ultimately prevent threats.
Remember, security is an ongoing journey, demanding constant vigilance and adaptation. Let us embrace this challenge, fortifying our digital fortresses and ensuring a secure future for our data and our users.