Server security incident response plan: steps to take in case of a breach – Server security incident response plans are essential in today’s digital landscape, where cyber threats are increasingly sophisticated. A well-defined plan can help organizations minimize the damage and disruption caused by a server breach, protecting valuable data, financial resources, and reputation.
This guide Artikels the critical steps involved in creating and implementing a comprehensive server security incident response plan, covering preparation, detection, containment, recovery, and post-incident review.
The importance of a server security incident response plan cannot be overstated. In the event of a breach, a well-prepared organization can respond quickly and effectively, limiting the impact on its operations and reputation. A comprehensive plan includes a clear understanding of potential threats, the roles and responsibilities of different teams, and the necessary tools and resources for a successful response.
Key Components of a Server Security Incident Response Plan: Server Security Incident Response Plan: Steps To Take In Case Of A Breach
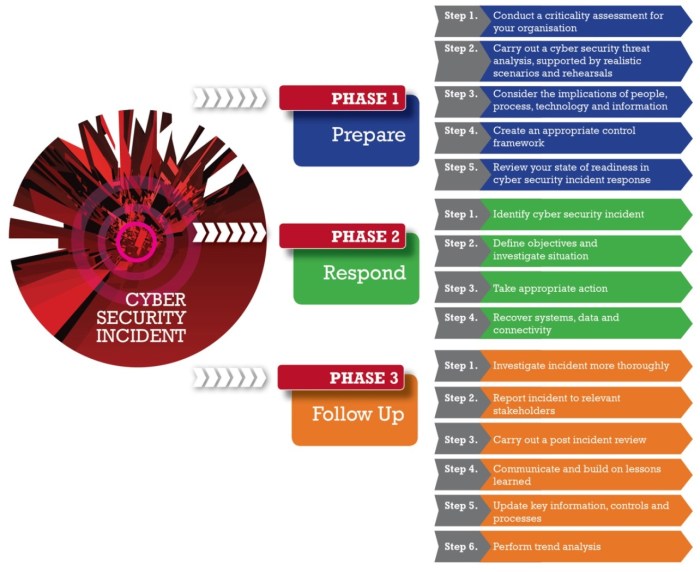
A comprehensive server security incident response plan is crucial for organizations to mitigate the impact of security breaches and ensure business continuity. It Artikels the steps to be taken in the event of a security incident, from detection to recovery and post-incident analysis.
A comprehensive server security incident response plan should include not only steps to mitigate damage but also proactive measures to prevent breaches. This includes carefully selecting hardware and software that meet the specific needs of the server, such as a dedicated server for gaming, which requires robust performance and reliable connectivity.
Dedicated server for gaming: choosing the right hardware and software offers valuable insights into these considerations. By investing in the right infrastructure and implementing stringent security protocols, you can significantly reduce the risk of a server breach and ensure a seamless gaming experience.
This plan acts as a roadmap for responding to threats effectively and efficiently.
The Stages of Incident Response
The incident response process is typically divided into five distinct stages, each with specific activities, roles, and resources. These stages ensure a systematic and coordinated approach to handling security incidents.
A robust server security incident response plan is crucial for any organization, especially when considering the choice between a dedicated server and a VPS. While a dedicated server offers greater control and security, a VPS can be more cost-effective.
The decision of which type of server is best for your business ultimately depends on your specific needs and the level of security you require. Ultimately, regardless of your choice, a well-defined incident response plan is essential for mitigating the impact of a breach and ensuring business continuity.
Dedicated server vs VPS: which is better for your business? can help you make an informed decision, but remember, a proactive security posture is paramount in today’s digital landscape.
| Stage | Activities | Roles and Responsibilities | Tools and Resources |
|---|---|---|---|
| Preparation |
|
|
|
| Detection |
|
|
|
| Containment |
|
|
|
| Recovery |
|
|
|
| Post-Incident Review |
|
|
|
Preparation and Planning
A robust server security incident response plan must be grounded in proactive preparation. This involves not only anticipating potential threats but also establishing a comprehensive framework to address them effectively. This section delves into the critical steps involved in preparing for a server security incident.
Risk Assessment
A thorough risk assessment is the cornerstone of effective security planning. This process involves identifying potential threats, analyzing their likelihood and impact, and prioritizing vulnerabilities based on their criticality. The goal is to gain a clear understanding of the potential risks to server systems and to allocate resources accordingly.
- Identify potential threats: This includes internal threats such as accidental errors or malicious insider activity, as well as external threats like cyberattacks, malware, and data breaches.
- Assess the likelihood and impact of each threat: This involves evaluating the probability of each threat occurring and the potential consequences of a successful attack.
- Prioritize vulnerabilities based on their criticality: Focus on addressing the vulnerabilities that pose the greatest risk to the organization.
Security Policies
Clearly defined security policies are essential for guiding server security practices and ensuring consistency across the organization. These policies should address key areas such as user access control, data protection, incident reporting, and system hardening.
A robust server security incident response plan is crucial for any organization, especially those managing high-traffic websites. While proactive security measures like firewalls and intrusion detection systems are essential, a well-defined response plan ensures swift and effective action in the event of a breach.
Optimizing server performance, as outlined in Dedicated server for high-traffic websites: performance optimization , is a key aspect of mitigating vulnerabilities and ensuring the website remains accessible during a security incident. A comprehensive response plan should include clear steps for containment, investigation, recovery, and communication, ensuring a swift and efficient resolution to minimize downtime and potential data loss.
- User access control: Policies should Artikel procedures for granting and revoking user access to server systems, based on the principle of least privilege.
- Data protection: Policies should define how sensitive data is classified, stored, and protected, including encryption and access controls.
- Incident reporting: Policies should establish clear procedures for reporting security incidents, ensuring timely and accurate communication to relevant stakeholders.
- System hardening: Policies should Artikel measures to strengthen server security, including patching vulnerabilities, disabling unnecessary services, and implementing strong passwords.
Security Controls, Server security incident response plan: steps to take in case of a breach
Implementing security controls is critical to mitigating server vulnerabilities and reducing the risk of security incidents. These controls can be categorized as technical, administrative, and physical.
Technical Controls
- Firewalls: Act as a barrier between the server and external networks, blocking unauthorized access.
- Intrusion detection and prevention systems (IDS/IPS): Monitor network traffic for suspicious activity and can block or alert on potential threats.
- Antivirus and anti-malware software: Protect servers from malicious software that can compromise security.
- Data loss prevention (DLP): Prevents sensitive data from leaving the organization’s network without authorization.
- Encryption: Protects data at rest and in transit, making it unreadable to unauthorized individuals.
- Multi-factor authentication (MFA): Adds an extra layer of security by requiring users to provide multiple forms of authentication, such as a password and a one-time code.
- Regular patching and updates: Keeps software up-to-date with the latest security patches, addressing known vulnerabilities.
Administrative Controls
- Security awareness training: Educates employees on security best practices and how to identify and report potential threats.
- Strong password policies: Enforces the use of complex passwords and regular password changes.
- Account management: Ensures proper account creation, management, and deactivation procedures.
- Change management: Controls changes to server configurations and applications, reducing the risk of unintended security vulnerabilities.
- Regular security audits: Evaluate the effectiveness of security controls and identify potential weaknesses.
Physical Controls
- Physical security: Secure server rooms and data centers with access control measures, surveillance systems, and environmental monitoring.
- Data backups: Regularly back up critical data to ensure recovery in case of a security incident.
- Disaster recovery planning: Develop a plan to restore critical systems and data in the event of a disaster or security breach.
Security Audits and Penetration Testing
Regular security audits and penetration testing are essential for identifying and addressing potential weaknesses in server security. These assessments provide an independent evaluation of the effectiveness of security controls and can uncover vulnerabilities that may have been overlooked.
- Security audits: Comprehensive reviews of security policies, procedures, and controls to ensure compliance with industry best practices and organizational standards.
- Penetration testing: Simulates real-world attacks to identify vulnerabilities and assess the effectiveness of security controls.
Containment and Mitigation
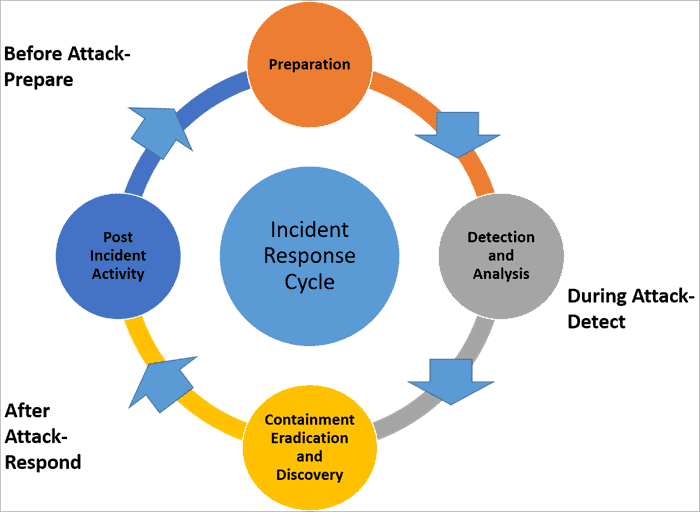
Containment and mitigation are crucial steps in responding to a server security incident. They aim to limit the impact of the breach, prevent further damage, and restore affected systems to a secure state. This process involves isolating compromised systems, controlling the spread of the incident, and implementing measures to minimize the potential for future attacks.
Isolating Compromised Systems
Isolating compromised systems is a critical first step in containing a server security incident. This involves disconnecting the affected systems from the network, preventing further communication and data transfer. This step is essential to prevent the attacker from gaining access to sensitive data on other systems or spreading the attack to other parts of the network.
A robust server security incident response plan is essential for any organization, especially those handling sensitive data or critical operations. While focusing on immediate actions like isolating the affected system and containing the breach, it’s crucial to consider the long-term implications of a data breach, particularly for businesses that rely heavily on cloud-based services.
Understanding the bandwidth and storage requirements for video streaming, as outlined in this detailed resource Cloud hosting for video streaming: bandwidth and storage requirements , can help inform your incident response plan by identifying potential vulnerabilities and mitigating future risks associated with data loss or service disruptions.
- Network Segmentation:Implementing network segmentation can help limit the impact of a breach by creating separate networks for different groups of systems. This prevents the spread of an attack from one network to another. For example, separating sensitive data systems from public-facing servers can prevent attackers from accessing critical data even if they compromise the public-facing servers.
A robust server security incident response plan is essential for any organization, but it takes on added importance in the cloud environment. While cloud providers offer robust security measures, it’s crucial to understand your responsibilities and how to react in case of a breach.
Understanding the benefits of cloud hosting, such as scalability and redundancy, as outlined in Cloud hosting for developers: features and benefits , can inform your incident response plan. For example, leveraging cloud backups can significantly speed up recovery from a data breach, minimizing downtime and potential financial losses.
- Firewalls:Firewalls can be used to block access to compromised systems from the network, preventing further communication and data transfer. This can help limit the spread of the attack and prevent attackers from gaining access to other systems.
- Intrusion Detection and Prevention Systems (IDS/IPS):These systems can monitor network traffic for suspicious activity and block potential attacks. They can be used to detect and block attacks targeting compromised systems, preventing further damage.
Limiting the Impact of the Breach
Limiting the impact of a breach involves taking steps to minimize the potential damage caused by the incident. This may involve identifying and containing the attack, restoring compromised systems, and recovering lost data.
- Data Backup and Recovery:Having regular backups of critical data is essential for recovery after a breach. These backups can be used to restore data that may have been compromised or deleted by the attacker.
- Incident Response Team:An incident response team should be responsible for coordinating containment efforts and communicating with stakeholders. The team should have the expertise and resources to quickly identify and contain the breach, minimize damage, and restore affected systems.
- Forensics Analysis:After containing the breach, a forensic analysis should be conducted to determine the extent of the damage and identify the attacker’s methods. This information can be used to improve security measures and prevent future attacks.
Incident Response Team Coordination
The incident response team plays a crucial role in coordinating containment efforts and communicating with stakeholders. The team should have a clear understanding of the organization’s security policies and procedures, and should be able to effectively communicate with technical and non-technical stakeholders.
- Communication Plan:The incident response team should have a communication plan in place to ensure that all stakeholders are informed of the situation and the steps being taken to contain the breach. This includes communicating with affected users, senior management, and external parties, such as law enforcement or security vendors.
- Roles and Responsibilities:The incident response team should have clearly defined roles and responsibilities. This ensures that everyone understands their role in the incident response process and that there is no duplication of effort.
- Escalation Procedures:The incident response team should have escalation procedures in place to ensure that senior management is informed of the situation and that appropriate action is taken. This includes reporting on the progress of the incident response, potential impact on the organization, and any decisions made.
Post-Incident Review and Improvement
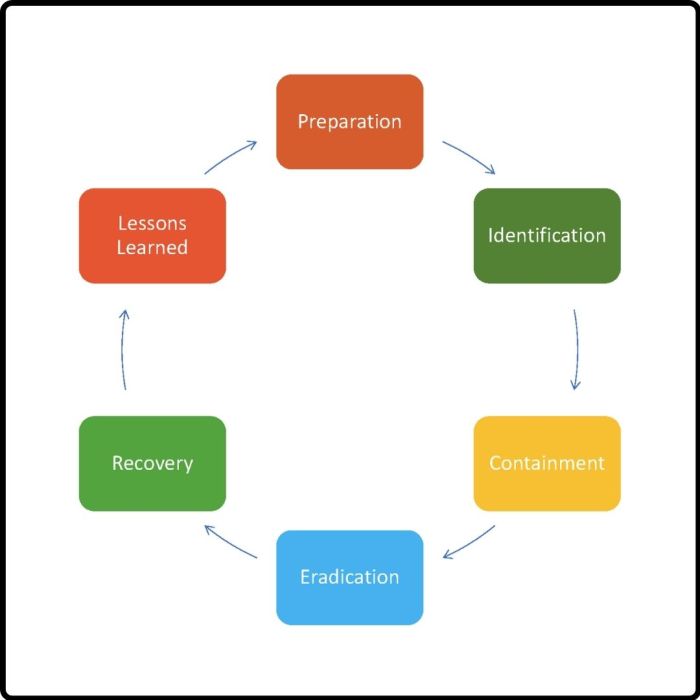
A post-incident review is not a mere formality; it’s a crucial step in strengthening your organization’s security posture. By meticulously examining the details of a security incident, you can uncover weaknesses and vulnerabilities, identify areas for improvement, and ultimately enhance your incident response capabilities.
Importance of Post-Incident Review
The post-incident review is essential for several reasons. It allows you to:
- Identify the root cause of the incident and understand the chain of events that led to the breach.
- Evaluate the effectiveness of your existing security controls and identify gaps in your defenses.
- Assess the performance of your incident response team and identify areas for improvement in communication, coordination, and decision-making.
- Document lessons learned and implement changes to prevent similar incidents from occurring in the future.
Key Areas of Focus
A comprehensive post-incident review should focus on several key areas, including:
Incident Response Effectiveness
The review should assess the effectiveness of your incident response plan and identify areas for improvement.
- Were the response procedures followed correctly and efficiently?
- Were the necessary resources available and deployed effectively?
- Were the communication channels clear and timely?
- Were the appropriate stakeholders involved in the response process?
Security Controls
The review should examine the effectiveness of your existing security controls, including:
- Were the controls in place adequate to prevent the incident?
- Were the controls properly configured and maintained?
- Were the controls bypassed or circumvented by the attacker?
- Were there any weaknesses in the controls that contributed to the incident?
Communication Protocols
Effective communication is vital during a security incident. The review should evaluate your communication protocols and identify areas for improvement:
- Were communication channels clear and timely?
- Were all stakeholders informed in a timely manner?
- Were the communication messages accurate and consistent?
- Were there any communication breakdowns that hindered the response effort?
Organizational Preparedness
The review should assess your organization’s overall preparedness for security incidents:
- Did your organization have a clear incident response plan in place?
- Was the plan adequately tested and updated?
- Were the necessary resources available to respond to the incident?
- Were employees trained on security awareness and incident response procedures?
Documenting and Communicating Findings
The findings of the post-incident review should be documented in a clear and concise manner. This documentation should include:
- A description of the incident, including the timeline of events, the attacker’s methods, and the impact of the incident.
- A detailed analysis of the root cause of the incident and the contributing factors.
- Recommendations for improvement, including specific actions to be taken to address the identified vulnerabilities and weaknesses.
- A plan for implementing the recommendations and tracking their effectiveness.
The findings of the post-incident review should be communicated to all relevant stakeholders, including:
- Senior management
- The incident response team
- Security personnel
- Affected departments
Final Review
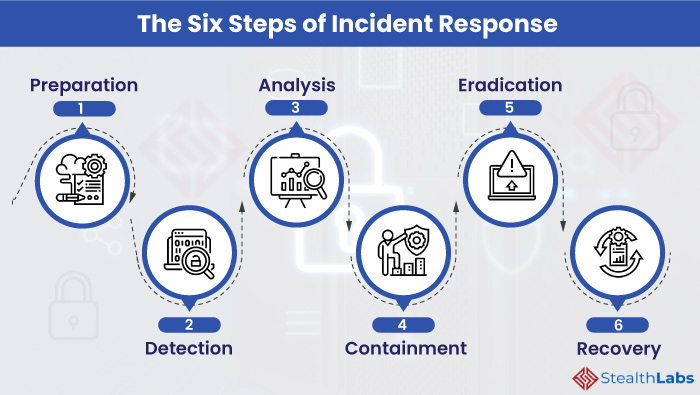
A server security incident response plan is a vital component of any organization’s cybersecurity strategy. By taking proactive steps to prepare for potential breaches, organizations can mitigate the risks and consequences of a security incident. This plan serves as a roadmap to guide response efforts, ensuring that organizations can effectively identify, contain, and recover from security incidents, minimizing disruption and protecting critical assets.

