Server security for remote access: secure connections and authentication – Secure remote access: secure connections and authentication – this is the foundation of a robust server security strategy. Imagine a world where sensitive data is easily accessible to anyone with a connection. This is the reality for organizations that neglect proper security measures for remote access.
From data breaches to malicious attacks, the consequences of insecure access can be devastating.
This guide delves into the essential components of securing remote access to servers. We’ll explore the importance of encryption protocols like SSH and SSL/TLS to establish secure connections, and delve into the different authentication methods that can be used to verify user identities.
Furthermore, we’ll examine access control measures, best practices for securing remote access, and advanced security measures that can further strengthen your server security posture.
Secure Connections
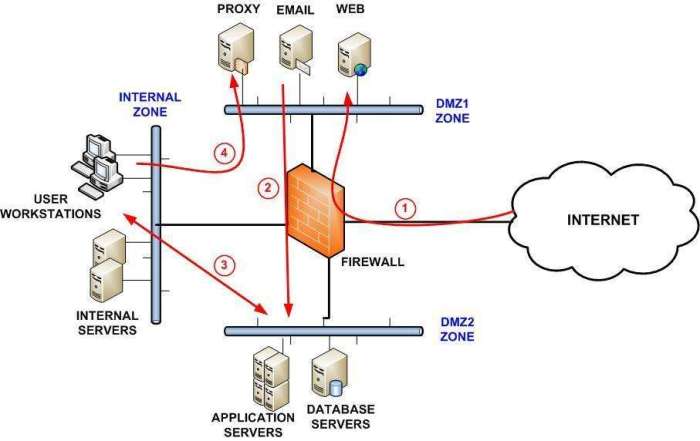
In the realm of remote access, establishing a secure connection is paramount. This ensures that sensitive information transmitted between the remote device and the server remains confidential and protected from unauthorized access. Encryption plays a pivotal role in achieving this security objective.
Encryption in Securing Remote Access
Encryption is the process of transforming data into an unreadable format, making it incomprehensible to anyone without the appropriate decryption key. This encryption process is applied to all data transmitted over the network, effectively creating a secure tunnel that safeguards sensitive information.
When it comes to server security for remote access, secure connections and robust authentication are paramount. This is especially crucial for high-traffic WordPress websites, which are often targeted by cyberattacks. Choosing the right cloud hosting provider can significantly enhance your website’s security posture.
Best cloud hosting for WordPress websites with high traffic often offers advanced security features like firewalls, intrusion detection systems, and regular security updates, further bolstering your defenses against potential threats. By implementing these measures, you can ensure your website remains secure and accessible to your users.
Comparison of Encryption Protocols, Server security for remote access: secure connections and authentication
Different encryption protocols offer varying levels of security and performance. Here’s a comparison of some commonly used protocols:
- SSH (Secure Shell): SSH is a widely adopted protocol for secure remote access and file transfer. It uses public-key cryptography to establish secure connections and encrypt all data transmitted between the client and server. SSH offers strong authentication and confidentiality, making it suitable for sensitive operations.
- SSL/TLS (Secure Sockets Layer/Transport Layer Security): SSL/TLS is a protocol designed for secure communication over the internet. It uses certificates issued by trusted authorities to authenticate servers and encrypt data. SSL/TLS is commonly used for web browsing, email, and other internet-based applications. It offers robust encryption and authentication capabilities.
Configuring Secure Connections
SSH Configuration
1. Generate SSH Keys On the client machine, use the `ssh-keygen` command to generate a public and private key pair.
2. Copy Public Key to Server Transfer the public key to the server, typically by placing it in the authorized_keys file within the user’s home directory.
3. Connect to Server Use the `ssh` command with the username and server address to establish a secure connection.
SSL/TLS Configuration
1. Obtain SSL Certificate Purchase an SSL certificate from a trusted Certificate Authority (CA).
2. Install Certificate on Server Install the certificate and its private key on the web server.
3. Configure Web Server Configure the web server (e.g., Apache, Nginx) to use SSL/TLS for all traffic.
Authentication: Server Security For Remote Access: Secure Connections And Authentication
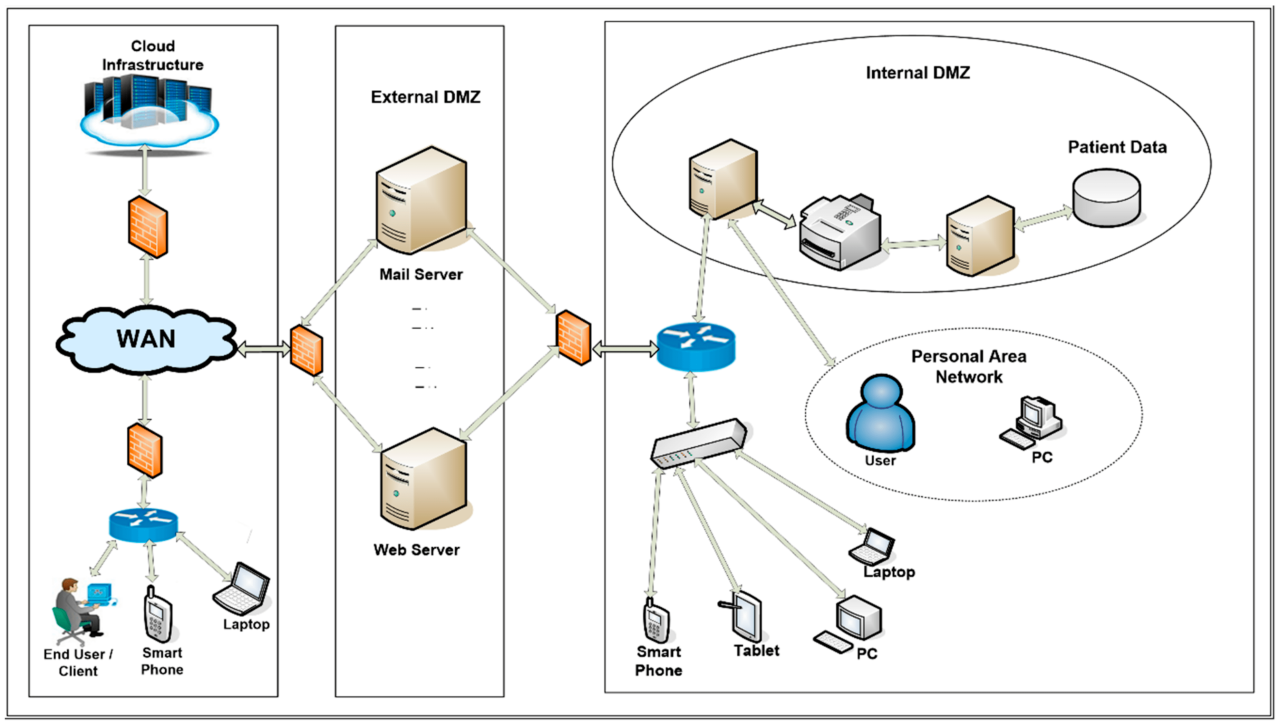
Authentication is the process of verifying the identity of a user or device trying to access a system. It’s a crucial aspect of securing remote access, ensuring that only authorized individuals can gain entry. This section explores various authentication methods and their effectiveness, delves into the advantages and disadvantages of Public Key Infrastructure (PKI) for authentication, and Artikels a secure authentication system design.
Password-Based Authentication
Password-based authentication is the most common method, where users provide a username and password to gain access. However, passwords can be easily compromised if they are weak or reused across multiple accounts.
Password Strength
Strong passwords are essential for security. They should be at least 12 characters long, include a mix of uppercase and lowercase letters, numbers, and symbols, and should not be easily guessable.
Password Management
Users should use a password manager to store and generate strong, unique passwords for each account. This helps prevent password reuse and makes it easier to remember complex passwords.
Securing remote access to your servers is paramount, especially when dealing with sensitive data or critical applications. This involves implementing robust authentication protocols and encrypting all communication channels. For gaming servers, the need for secure remote access is even more crucial, as players expect seamless and reliable gameplay.
Cloud hosting, as discussed in Cloud hosting for gaming servers: performance and reliability , can offer a powerful solution, but it’s vital to ensure that your cloud infrastructure is properly secured to protect against unauthorized access and data breaches.
Multi-Factor Authentication (MFA)
MFA adds an extra layer of security by requiring users to provide two or more authentication factors. This makes it significantly harder for unauthorized individuals to gain access, even if they have stolen a password.
Types of MFA
- Something you know:This is the traditional password-based authentication.
- Something you have:This could be a physical token, a mobile app, or a hardware security key.
- Something you are:This involves biometrics, such as fingerprint scanning, facial recognition, or iris scanning.
MFA Benefits
- Increased security:MFA makes it much harder for unauthorized individuals to gain access, even if they have stolen a password.
- Reduced risk of account compromise:MFA helps prevent account compromise, even if one authentication factor is compromised.
- Improved compliance:MFA is often required by industry regulations and standards, such as PCI DSS and HIPAA.
Biometric Authentication
Biometric authentication uses unique biological characteristics to verify identity. It can be more secure than traditional methods because it is difficult to forge or steal.
Biometric Methods
- Fingerprint scanning:This method compares a user’s fingerprint to a stored template.
- Facial recognition:This method uses facial features to identify a user.
- Iris scanning:This method uses the unique patterns in a user’s iris to verify identity.
Biometric Authentication Benefits
- Enhanced security:Biometric authentication is more secure than traditional methods because it is difficult to forge or steal.
- Improved user experience:Biometric authentication can be more convenient and user-friendly than traditional methods, especially for mobile devices.
- Increased efficiency:Biometric authentication can automate the authentication process, which can improve efficiency.
Public Key Infrastructure (PKI)
PKI is a system that uses digital certificates to verify the identity of users and devices. It provides a secure and reliable way to authenticate users and encrypt data.
PKI Advantages
- Strong authentication:PKI provides strong authentication by using digital certificates, which are difficult to forge or steal.
- Data encryption:PKI can be used to encrypt data, ensuring that only authorized individuals can access it.
- Non-repudiation:PKI provides non-repudiation, which means that users cannot deny sending or receiving data.
PKI Disadvantages
- Complexity:PKI can be complex to implement and manage.
- Cost:PKI can be expensive to implement and maintain.
- Trust:PKI relies on a chain of trust, which can be vulnerable to attacks.
Secure Authentication System Design
A secure authentication system should incorporate multiple layers of security, including strong passwords, multi-factor authentication, and access control mechanisms.
Securing remote access to your server is crucial, especially when you’re migrating your website. Implementing robust security measures like strong authentication and encrypted connections is essential, especially when transitioning from shared hosting to a cloud platform. If you’re considering a move to cloud hosting, be sure to check out this comprehensive guide on how to migrate a website from shared hosting to cloud hosting , which will help you ensure a smooth and secure transition.
Once you’ve successfully migrated, don’t forget to continue prioritizing server security by regularly updating your software and implementing multi-factor authentication for added protection.
Strong Passwords
Users should be required to create strong passwords that are at least 12 characters long and include a mix of uppercase and lowercase letters, numbers, and symbols.
Multi-Factor Authentication (MFA)
MFA should be implemented for all users, requiring them to provide two or more authentication factors to gain access.
Access Control Mechanisms
Access control mechanisms should be used to restrict access to specific resources based on user roles and permissions.
Access Control and Permissions
Implementing robust access control measures is crucial for safeguarding your server and its resources. By carefully defining who can access what, you minimize the risk of unauthorized activity and data breaches. This section explores the concept of least privilege and its importance in server security.
It also demonstrates how to implement Access Control Lists (ACLs) to restrict user access to specific resources. Finally, it Artikels common user roles and their corresponding permissions for remote access.
Least Privilege
The principle of least privilege dictates that users should only have access to the resources they absolutely need to perform their tasks. This minimizes the potential damage caused by malicious actors or accidental misuse. By granting only necessary permissions, you reduce the attack surface and limit the scope of potential harm.
For example, a user who only needs to access specific files for reporting should not have administrative privileges on the server.
Implementing Access Control Lists (ACLs)
Access Control Lists (ACLs) are a powerful mechanism for granularly controlling access to server resources. They define specific permissions for individual users or groups, allowing you to precisely control who can access what and how.
- Defining Permissions:ACLs allow you to specify various permissions, such as read, write, execute, and delete. This enables you to tailor access based on the specific needs of each user or group. For example, you might grant read-only access to certain files for users who need to view reports, while granting write access to users responsible for data entry.
- Applying ACLs:ACLs can be applied to various resources, including files, directories, and network shares. This allows you to control access at different levels of granularity. For instance, you might apply an ACL to a specific directory to restrict access to only authorized personnel.
- Example:Consider a scenario where you want to restrict access to a sensitive configuration file. You can create an ACL that grants read and write access only to administrators, while denying access to all other users. This ensures that only authorized personnel can modify the file, safeguarding its integrity.
Common User Roles and Permissions
Here’s a table outlining common user roles and their corresponding permissions for remote access:
| User Role | Permissions |
|---|---|
| Administrator | Full access to all resources, including system configuration, user management, and data manipulation. |
| Developer | Access to specific development environments, code repositories, and testing resources. |
| Analyst | Read-only access to data and reports for analysis and reporting purposes. |
| Guest | Limited access to specific public resources, such as websites or public files. |
Security Best Practices for Remote Access
Remote access security is a multifaceted area, requiring proactive measures to minimize vulnerabilities and safeguard sensitive data. This section delves into essential best practices to ensure the secure operation of remote access systems.
Regular Security Audits and Vulnerability Scanning
Regular security audits are essential for identifying and mitigating potential vulnerabilities in remote access systems. They involve a thorough examination of system configurations, user permissions, and security protocols. Vulnerability scanning is a complementary practice that automatically identifies weaknesses and potential exploits in software and hardware components.
Securing your server for remote access is paramount, especially when handling sensitive data like video editing projects. Robust authentication and secure connections are essential to prevent unauthorized access. Consider the processing power and storage requirements needed for your video editing workflow, as these factors can influence your server setup.
A dedicated server, as discussed in Dedicated server for video editing: processing power and storage requirements , can provide the necessary resources for efficient video editing. Once you’ve established your server infrastructure, prioritize security measures to protect your work and ensure smooth collaboration.
- Conduct regular security audits at least quarterly or more frequently for high-risk systems.
- Employ automated vulnerability scanning tools to identify and prioritize vulnerabilities.
- Remediate vulnerabilities promptly, applying necessary patches and security updates.
Patch Management
Patch management is a critical aspect of remote access security. Software vendors regularly release security patches to address vulnerabilities discovered in their products. Timely application of these patches is essential to prevent exploitation of known weaknesses.
- Establish a centralized patch management system to track and apply updates efficiently.
- Prioritize critical security patches and apply them as soon as possible.
- Test patches in a controlled environment before deploying them to production systems.
Strong Passwords and Multi-Factor Authentication
Strong passwords are a fundamental security measure for remote access accounts. Passwords should be complex, combining uppercase and lowercase letters, numbers, and special characters. Multi-factor authentication (MFA) adds an extra layer of security by requiring users to provide multiple forms of identification, such as a password and a one-time code generated by a mobile app.
- Enforce strong password policies that require a minimum length, complexity, and regular rotation.
- Implement multi-factor authentication (MFA) for all remote access accounts.
- Use a password manager to securely store and manage complex passwords.
Security Incident Detection and Response
Security incidents can occur despite implementing strong security measures. It is crucial to have a robust incident detection and response plan in place. This plan should Artikel procedures for identifying, containing, and remediating security breaches.
- Implement intrusion detection and prevention systems (IDS/IPS) to monitor network traffic for suspicious activity.
- Use security information and event management (SIEM) tools to aggregate and analyze security logs.
- Develop a comprehensive incident response plan that includes steps for containment, investigation, and recovery.
Securing remote access to servers is crucial, especially when dealing with sensitive scientific data. This involves implementing strong authentication methods and encrypting data transmission. For researchers who need to crunch massive datasets and run complex simulations, a dedicated server for scientific research can provide the necessary computational power.
However, ensuring secure access to this powerful resource remains paramount, as any breach could compromise years of research and valuable data.
Advanced Security Measures
Now that we’ve established a solid foundation with secure connections, authentication, and access control, let’s delve into some advanced security measures that can further enhance your remote access setup. These measures are crucial for safeguarding sensitive data and systems, especially in environments where remote access is essential.
Network Segmentation
Network segmentation is a powerful technique that involves dividing your network into smaller, isolated segments. This isolation helps limit the impact of a security breach, preventing attackers from spreading laterally across your entire network. When it comes to remote access, network segmentation plays a critical role by isolating sensitive servers from external networks.
Imagine a scenario where a remote user’s device is compromised. Without network segmentation, an attacker could potentially gain access to your entire network, including sensitive servers. However, with network segmentation, the compromised device would only be able to access the specific segment it’s connected to, preventing the attacker from reaching other parts of your network.
- Benefits of Network Segmentation
- Reduced Attack Surface:Isolating sensitive servers reduces the potential targets for attackers.
- Improved Security Posture:Segmentation helps create a more secure network by limiting the spread of malware and other threats.
- Enhanced Compliance:Many industry regulations, such as HIPAA and PCI DSS, require network segmentation to protect sensitive data.
Intrusion Detection and Prevention Systems (IDS/IPS)
Intrusion detection and prevention systems (IDS/IPS) are essential tools for monitoring network traffic and detecting suspicious activity. An IDS passively monitors network traffic, identifying potential threats and alerting administrators. An IPS takes a more proactive approach, blocking malicious traffic before it can reach your systems.
In the context of remote access, IDS/IPS can play a vital role in identifying and preventing unauthorized access attempts. They can analyze network traffic for signs of known attacks, such as brute-force login attempts or malware downloads. By detecting and blocking these threats, IDS/IPS can help protect your systems from unauthorized access.
- Benefits of IDS/IPS for Remote Access
- Early Threat Detection:IDS/IPS can identify suspicious activity before it causes significant damage.
- Real-Time Protection:IPS can block malicious traffic in real-time, preventing attacks from reaching your systems.
- Enhanced Security Posture:IDS/IPS provide an extra layer of security, supplementing other security measures.
Security Information and Event Management (SIEM)
Security information and event management (SIEM) is a comprehensive security solution that collects and analyzes security data from various sources, including firewalls, IDS/IPS, and servers. SIEM provides a centralized view of security events, enabling security teams to identify and respond to threats quickly and efficiently.
For remote access, SIEM plays a critical role in monitoring and analyzing user activity. It can track login attempts, data access patterns, and other events related to remote access. By analyzing this data, SIEM can detect anomalies that may indicate malicious activity or unauthorized access.
It can also help identify security vulnerabilities and provide insights into user behavior.
- Benefits of SIEM for Remote Access
- Centralized Security Monitoring:SIEM provides a single pane of glass for security monitoring, simplifying threat detection and response.
- Comprehensive Threat Detection:SIEM analyzes data from multiple sources, providing a holistic view of security events.
- Automated Incident Response:SIEM can automate certain incident response tasks, such as blocking malicious IP addresses.
Security Awareness and Training
In the realm of remote access, bolstering security measures is not solely dependent on technological implementations. It is equally imperative to equip users with the knowledge and understanding of secure practices. A well-structured security awareness program serves as a crucial cornerstone, empowering individuals to safeguard sensitive data and systems from potential threats.
Importance of User Education
Security awareness training plays a pivotal role in mitigating the risks associated with remote access. By fostering a culture of security consciousness among users, organizations can effectively minimize vulnerabilities arising from human error or negligence. This training equips individuals with the necessary knowledge to identify and avoid potential threats, promoting a proactive approach to security.
Key Security Awareness Topics
To ensure comprehensive coverage of critical security concepts, a well-defined curriculum should encompass the following key topics:
Strong Password Management
- Emphasize the importance of creating strong passwords that are unique for each account and avoid common patterns or personal information.
- Encourage the use of password managers to securely store and manage passwords, reducing the risk of compromise.
- Reinforce the importance of regularly changing passwords, especially for high-risk accounts.
Phishing and Social Engineering Awareness
- Educate users about the tactics employed by phishers to deceive individuals into revealing sensitive information.
- Provide examples of phishing emails, websites, and social media posts to enhance user recognition and vigilance.
- Train users to verify the authenticity of communications before clicking on links or opening attachments.
Secure Remote Access Practices
- Emphasize the importance of using secure VPN connections for all remote access activities.
- Encourage the use of multi-factor authentication (MFA) to enhance account security.
- Train users to recognize and report suspicious activity or unauthorized access attempts.
Data Security and Confidentiality
- Educate users about the importance of data confidentiality and the potential consequences of unauthorized data disclosure.
- Train users on appropriate data handling practices, such as avoiding the sharing of sensitive information over unsecured channels.
- Reinforce the importance of adhering to data security policies and procedures.
Mobile Device Security
- Emphasize the importance of using strong passwords and biometrics for mobile devices.
- Encourage users to install and keep security software up-to-date on their mobile devices.
- Train users to be cautious about downloading apps from untrusted sources.
Effective Security Awareness Training
To maximize the effectiveness of security awareness training, consider the following strategies:
Interactive and Engaging Content
- Utilize interactive training modules, simulations, and real-world scenarios to engage users and enhance knowledge retention.
- Incorporate quizzes, games, and other interactive elements to make learning more enjoyable and memorable.
Regular Refreshers and Updates
- Conduct regular security awareness training sessions to reinforce key concepts and address emerging threats.
- Update training materials periodically to reflect evolving security landscapes and best practices.
Practical Exercises and Case Studies
- Include practical exercises and case studies that allow users to apply their knowledge in real-world scenarios.
- Provide opportunities for users to practice secure remote access practices and identify potential vulnerabilities.
Feedback and Evaluation
- Collect feedback from users to assess the effectiveness of training programs and identify areas for improvement.
- Conduct periodic evaluations to measure user understanding and retention of key security concepts.
Concluding Remarks
Securing remote access to servers is a multi-faceted endeavor that requires a comprehensive approach. By implementing strong encryption, robust authentication, and access control mechanisms, you can significantly reduce the risk of unauthorized access and protect your valuable data. Remember, a proactive security strategy is essential for safeguarding your servers and maintaining a secure digital environment.
Continuous vigilance, regular security audits, and staying informed about the latest security threats are key to staying ahead of potential vulnerabilities.

