Server security vulnerabilities: common threats and mitigation strategies sets the stage for this enthralling narrative, offering readers a glimpse into a story that is rich in detail and brimming with originality from the outset. In today’s digital landscape, where data is king and servers are the throne, security is paramount.
But these digital fortresses are not invincible, and cybercriminals are constantly seeking vulnerabilities to exploit.
From malicious software to database exploits, the threats to server security are diverse and ever-evolving. The consequences of a successful attack can be devastating, ranging from data breaches and financial losses to reputational damage and even legal repercussions. But fear not, for this guide will equip you with the knowledge and strategies to fortify your digital defenses and protect your valuable assets.
Common Server Security Threats
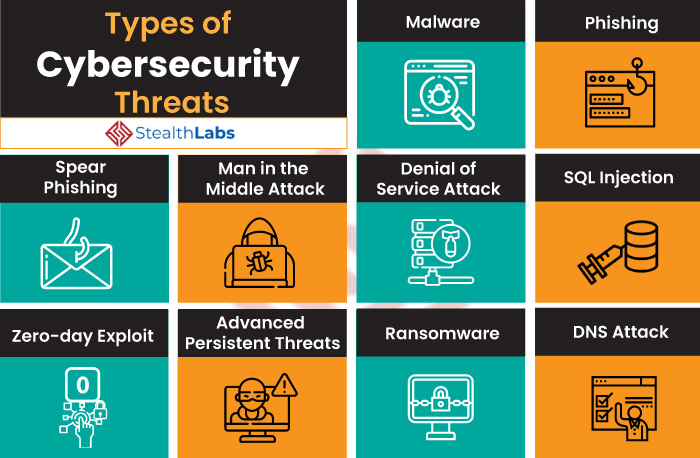
Servers are the backbone of modern technology, powering everything from websites and applications to critical infrastructure. However, these powerful machines are also vulnerable to various security threats, which can have devastating consequences. Understanding these threats is crucial for protecting your server infrastructure and ensuring the integrity of your data.
Malware, Server security vulnerabilities: common threats and mitigation strategies
Malware, short for malicious software, is designed to harm or exploit servers. It can take various forms, including viruses, ransomware, and trojans.
You gotta be on your toes with server security, bruv. Those pesky hackers are always looking for a way in. One way to beef up your defenses is by using a dedicated server for data storage and backup, like the ones mentioned here.
This way, even if your main server gets compromised, your data is safe and sound. So yeah, keep your security tight, and your data will be sweet.
- Viruses:These self-replicating programs can spread to other servers, corrupting files and disrupting operations.
- Ransomware:This type of malware encrypts data and demands payment for its decryption. It can cripple businesses by making their data inaccessible.
- Trojans:These programs disguise themselves as legitimate software but contain malicious code that can steal data, install backdoors, or grant remote access to attackers.
Malware can be spread through various methods, including email attachments, malicious websites, and compromised software. The motivations behind malware attacks vary, ranging from financial gain to espionage and disruption.
SQL Injection
SQL Injection is a common attack technique that exploits vulnerabilities in database queries. Attackers can inject malicious SQL code into input fields, allowing them to bypass security measures and gain unauthorized access to sensitive data.
Keeping your server safe from the baddies is a right chore, innit? You gotta be on top of those vulnerabilities, like SQL injection or DDoS attacks. But how you host your server can make a big difference. If you’re not sure whether to go with cloud hosting or a dedicated server , it’s worth thinking about the security implications.
Cloud providers often handle a lot of the security for you, but dedicated servers give you more control, which can be good or bad depending on your skills and resources.
For example, an attacker could inject malicious code into a login form to retrieve usernames and passwords stored in the database.
The impact of successful SQL Injection attacks can be significant, leading to data breaches, financial losses, and reputational damage.
Cross-Site Scripting (XSS)
Cross-Site Scripting (XSS) is a web security vulnerability that allows attackers to inject malicious scripts into websites. When a user visits the compromised website, their browser executes the malicious script, potentially allowing the attacker to steal user credentials, redirect users to malicious sites, or hijack their accounts.
Right, so you’re worried about your server getting hacked, yeah? Like, SQL injections, DDoS attacks, the whole shebang. Well, one way to beef up your security is by switching to cloud hosting. It’s a bit more complex, but check out this guide on how to migrate a website from shared hosting to cloud hosting.
Cloud providers usually have better security measures in place, and you’ll be less of a target for those nasty hackers.
Imagine an attacker injecting malicious code into a comment section on a website. When a user views the comment, the script executes, potentially stealing their cookies or other sensitive information.
Server security’s a right pain, innit? DDoS attacks, SQL injections, the whole shebang. But, if you’re slinging wares online, you gotta be on top of your game. Choosing the right cloud hosting is crucial, like having a proper fortress for your digital shop.
Check out this article on Choosing the right cloud hosting for e-commerce websites to get clued up. Once you’ve got your base sorted, you can focus on shoring up those security vulnerabilities, like a boss.
XSS attacks can have severe consequences, leading to data breaches, identity theft, and financial losses.
Denial of Service (DoS)
Denial of Service (DoS) attacks aim to overwhelm servers with traffic, making them unresponsive to legitimate users. Attackers can flood servers with requests, consume server resources, and disrupt services.
A common DoS attack involves sending a large number of requests to a server from multiple sources, effectively overloading the server and making it unavailable.
DoS attacks can be devastating for businesses, disrupting operations, causing financial losses, and damaging reputation.
Right, so you’ve got your server, but you’ve gotta keep it safe from the usual suspects: hackers, malware, the whole shebang. But what if you could offload that stress and get a top-notch performance boost at the same time?
That’s where Cloud hosting for gaming servers: performance and reliability comes in, offering reliable performance and security that’s practically bulletproof. So, ditch the server headaches and focus on what matters: keeping your game running smooth and your players happy.
Misconfiguration
Misconfiguration refers to incorrect server settings that can create security vulnerabilities. These vulnerabilities can be exploited by attackers to gain unauthorized access to servers or data.
- Weak passwords:Using easily guessable passwords can make servers vulnerable to brute-force attacks.
- Open ports:Unnecessary open ports can provide attackers with entry points to the server.
- Outdated software:Outdated software often contains known vulnerabilities that can be exploited by attackers.
Misconfiguration is often a result of human error or lack of awareness about security best practices.
Best Practices for Server Security
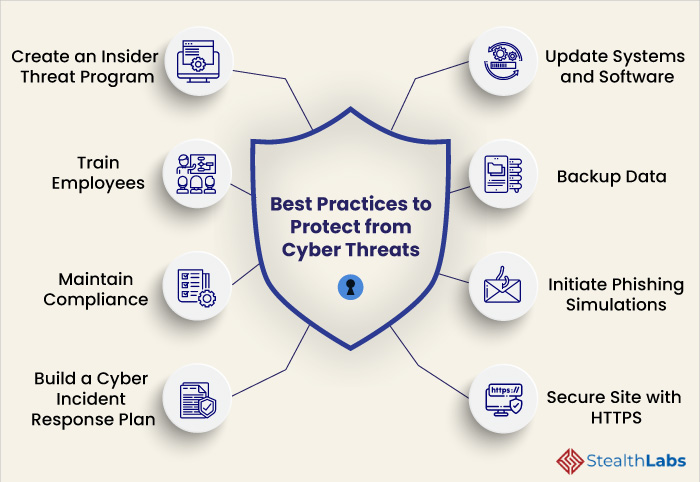
Server security is a continuous process that requires vigilance and proactive measures. By implementing a comprehensive security strategy, you can significantly reduce the risk of attacks and protect your valuable data and applications.
Secure Configuration of Operating Systems and Applications
Secure configuration involves setting up operating systems and applications with the most secure settings possible. This minimizes vulnerabilities and strengthens the overall security posture of your server.
- Disable unnecessary services and ports:By default, operating systems and applications often have many services and ports enabled. Disabling those that are not required for your server’s functionality reduces the attack surface, making it harder for attackers to exploit vulnerabilities.
- Apply security updates promptly:Software vendors regularly release security updates to patch vulnerabilities. Installing these updates as soon as they become available is crucial to prevent attackers from exploiting known weaknesses.
- Use strong passwords and multi-factor authentication:Strong passwords are essential for protecting user accounts. Implementing multi-factor authentication adds an extra layer of security by requiring users to provide two or more forms of authentication before granting access.
- Implement least privilege principle:Grant users only the minimum permissions necessary to perform their tasks. This principle limits the damage that can be caused if an account is compromised.
- Enable logging and monitoring:Actively monitor system logs for suspicious activity. This can help detect and respond to security incidents in a timely manner.
Secure User Account Management
Proper user account management is essential to prevent unauthorized access and data breaches.
- Use strong passwords and enforce password complexity:Strong passwords should be at least 12 characters long and include a mix of uppercase and lowercase letters, numbers, and symbols. Implement password complexity policies to encourage users to create strong passwords.
- Regularly review user accounts:Regularly review user accounts to ensure that they are still necessary and that users have appropriate permissions. Disable or delete accounts that are no longer needed.
- Implement account lockout policies:Configure account lockout policies to prevent brute-force attacks. This policy automatically locks out accounts after a certain number of failed login attempts.
- Use centralized identity and access management (IAM) solutions:Centralized IAM solutions simplify user account management by providing a single platform to manage user identities, permissions, and access controls.
Regular Security Audits and Vulnerability Assessments
Regular security audits and vulnerability assessments help identify potential security weaknesses in your server environment.
- Perform regular penetration testing:Penetration testing simulates real-world attacks to identify vulnerabilities that could be exploited by attackers. This helps identify weaknesses that might be missed by other security assessments.
- Use vulnerability scanning tools:Vulnerability scanning tools automatically scan your server for known vulnerabilities and provide detailed reports on identified weaknesses.
- Review security logs regularly:Regularly review security logs for suspicious activity. This can help identify potential attacks or unauthorized access attempts.
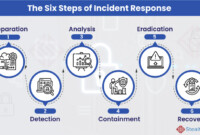
Incident Response Planning and Procedures
Having a well-defined incident response plan is crucial for responding to security incidents effectively.
- Develop a comprehensive incident response plan:This plan should Artikel the steps to be taken in the event of a security incident, including incident identification, containment, eradication, recovery, and lessons learned.
- Establish clear communication channels:Define clear communication channels for reporting and responding to security incidents. This ensures that all relevant parties are informed and coordinated during an incident.
- Conduct regular incident response drills:Regularly conduct incident response drills to test your plan and ensure that your team is prepared to handle real-world incidents effectively.
Conclusive Thoughts: Server Security Vulnerabilities: Common Threats And Mitigation Strategies

By understanding the common threats, implementing robust mitigation strategies, and embracing a culture of continuous improvement, we can effectively safeguard our servers and ensure the integrity of our digital world. So, let’s embark on this journey together, armed with knowledge and determination, to build a secure and resilient digital future.