In the ever-evolving landscape of cloud computing, safeguarding sensitive data and applications has become paramount. ‘Server security for cloud-based applications: best practices and considerations’ takes center stage, as organizations increasingly rely on cloud infrastructure for their operations. This exploration delves into the multifaceted realm of cloud security, examining best practices, addressing common vulnerabilities, and navigating the intricacies of data protection in a shared responsibility model.
From understanding the unique security challenges posed by cloud environments to implementing robust data encryption mechanisms, this comprehensive guide equips individuals and organizations with the knowledge and tools to secure their cloud assets effectively. Whether you’re a seasoned security professional or just starting your journey into cloud security, this exploration provides valuable insights and practical strategies to mitigate risks and ensure the integrity of your cloud-based applications.
Server Security Best Practices
Securing servers is crucial for protecting sensitive data and ensuring the integrity of cloud-based applications. Implementing robust security practices is essential to mitigate risks and maintain a secure environment. This section delves into best practices for securing operating systems and applications, emphasizing the importance of regular security patching and updates, and exploring the use of firewalls, intrusion detection systems, and other security tools.
Keeping your cloud apps safe is like protecting your sacred temple, right? You need to be extra careful with those digital offerings! But don’t worry, there are some awesome tips and tricks to keep everything secure. And if you’re thinking about setting up your own dedicated server, check out this awesome guide on Dedicated server security: essential steps and tools to make sure your virtual home is as protected as your real one.
No matter what you choose, remember to keep your digital world safe and sound, just like the ancient wisdom of Bali.
Operating System and Application Security
Operating systems and applications form the foundation of server infrastructure. It is essential to secure them effectively to prevent unauthorized access, malware infections, and data breaches.
- Implement Strong Password Policies:Enforce strong password policies for all user accounts, including root and administrator accounts. This includes using a combination of uppercase and lowercase letters, numbers, and symbols, and setting minimum password lengths. Strong passwords act as the first line of defense against unauthorized access.
- Enable Multi-Factor Authentication (MFA):MFA adds an extra layer of security by requiring users to provide two or more forms of authentication, such as a password and a one-time code generated by a mobile app. This significantly reduces the risk of unauthorized access, even if a password is compromised.
Keeping your cloud-based apps safe is a total vibe, like building a bamboo fortress in the jungle. But for serious gamers, you need the speed and reliability of a lightning strike, which is where Cloud hosting for gaming servers: performance and reliability comes in.
And remember, even the best servers need a strong security foundation, so make sure your cloud setup is locked down tight, like a Balinese temple guarded by fierce statues!
- Regularly Patch and Update Systems:Software vendors release security patches and updates to address vulnerabilities and fix bugs. Regularly patching and updating operating systems and applications is crucial to protect against known exploits and vulnerabilities. This includes installing updates for both the operating system and all installed software.
- Limit User Privileges:Principle of least privilege should be followed, meaning users should only have access to the resources they need to perform their tasks. This minimizes the potential impact of a compromised account, as a user with limited privileges cannot access sensitive data or systems.
- Secure Configuration:Proper configuration of operating systems and applications is essential for security. This involves disabling unnecessary services, strengthening default security settings, and configuring access control lists (ACLs) to restrict access to specific resources.
Importance of Regular Security Patching and Updates
Regular security patching and updates are critical for maintaining the security of servers and applications. Software vulnerabilities are constantly being discovered, and attackers are quick to exploit them. By applying security patches and updates promptly, organizations can mitigate these risks and prevent potential attacks.
- Patching and Updating Addresses Known Vulnerabilities:Security patches and updates are designed to address known vulnerabilities and fix security bugs. By applying these updates, organizations can close loopholes that attackers could exploit to gain unauthorized access or compromise systems.
- Reduce Attack Surface:Regular patching and updating reduce the attack surface by eliminating known vulnerabilities. This makes it more difficult for attackers to find and exploit weaknesses in systems.
- Maintain System Stability:Security updates often include bug fixes and performance enhancements that improve the overall stability and reliability of systems. This helps to prevent issues that could potentially lead to security vulnerabilities.
Firewalls, Intrusion Detection Systems, and Other Security Tools
Firewalls, intrusion detection systems (IDS), and other security tools play a vital role in securing server infrastructure. They act as the first line of defense against malicious traffic and unauthorized access attempts.
- Firewalls:Firewalls act as a barrier between a server and the external network, filtering incoming and outgoing traffic based on predefined rules. They block unauthorized access attempts and prevent malicious traffic from reaching the server.
- Network Firewalls:Network firewalls are deployed at the network perimeter, controlling traffic between the server network and the external world.
Keeping your cloud apps safe is like building a bamboo hut in the jungle – gotta be smart about it! Strong passwords, regular updates, and firewalls are your best defenses. But if you’re dealing with a ton of traffic, you might want to consider a dedicated server for better performance, like those discussed in this article on dedicated server optimization.
Ultimately, a secure and speedy cloud app is like a delicious nasi campur – satisfying on all levels!
- Host-Based Firewalls:Host-based firewalls are installed on individual servers and filter traffic at the operating system level.
- Network Firewalls:Network firewalls are deployed at the network perimeter, controlling traffic between the server network and the external world.
- Intrusion Detection Systems (IDS):IDS monitor network traffic for suspicious activity and alert administrators to potential threats. They analyze network traffic patterns and identify anomalies that could indicate an attack in progress.
- Network-Based IDS:Network-based IDS monitor traffic on the network and alert administrators to suspicious activity.
- Host-Based IDS:Host-based IDS monitor traffic on individual servers and alert administrators to suspicious activity.
- Anti-Malware Software:Anti-malware software scans systems for malware and other threats. It helps to prevent malware infections and remove existing malware from servers. Regularly updating anti-malware software is crucial to ensure it can detect and remove the latest threats.
- Security Information and Event Management (SIEM):SIEM solutions collect and analyze security data from various sources, such as firewalls, IDS, and servers. They provide a centralized view of security events and help administrators identify and respond to threats.
Network Security in the Cloud
Cloud-based applications rely heavily on secure network connectivity. This section explores critical network security considerations, including the use of virtual private networks (VPNs) and network segmentation, and best practices for safeguarding cloud network traffic.
Virtual Private Networks (VPNs)
VPNs establish secure connections between devices and networks over public networks, such as the internet. They encrypt data, masking its content and ensuring privacy during transmission.
- Data Encryption:VPNs employ encryption algorithms to transform data into an unreadable format, making it incomprehensible to unauthorized parties.
- Secure Tunneling:VPNs create a secure tunnel, encapsulating network traffic within a secure channel, protecting it from eavesdropping or interception.
- Access Control:VPNs enforce access controls, granting authorized users and devices access while preventing unauthorized access to sensitive data.
- Remote Access:VPNs enable secure remote access to corporate networks, allowing employees to work remotely while maintaining security.
Network Segmentation
Network segmentation involves dividing a network into smaller, isolated segments, each with its own security policies and controls. This approach enhances security by limiting the impact of security breaches and reducing the attack surface.
- Isolation:Network segmentation isolates sensitive data and applications, preventing unauthorized access from other segments.
- Controlled Access:Network segmentation allows for granular control over access, restricting communication between segments based on security policies.
- Attack Containment:Network segmentation limits the spread of malware or attacks, preventing them from affecting other segments of the network.
- Compliance:Network segmentation can assist organizations in meeting compliance requirements by isolating sensitive data and controlling access.
Best Practices for Securing Cloud Network Traffic
Securing cloud network traffic is crucial to protecting data and applications. Implementing these best practices can strengthen cloud network security.
- Firewall Rules:Implement strict firewall rules to block unauthorized access to cloud resources and restrict inbound and outbound traffic based on security policies.
- Network Intrusion Detection and Prevention Systems (IDS/IPS):Deploy IDS/IPS solutions to monitor network traffic for suspicious activity, detect potential threats, and prevent attacks.
- Secure Socket Layer (SSL)/Transport Layer Security (TLS):Use SSL/TLS encryption to protect sensitive data transmitted over the network, ensuring secure communication between applications and users.
- Network Segmentation:Implement network segmentation to isolate sensitive applications and data from other parts of the network, reducing the attack surface and mitigating the impact of breaches.
- Regular Security Audits:Conduct regular security audits to assess the effectiveness of security measures, identify vulnerabilities, and ensure compliance with security standards.
Security Monitoring and Incident Response
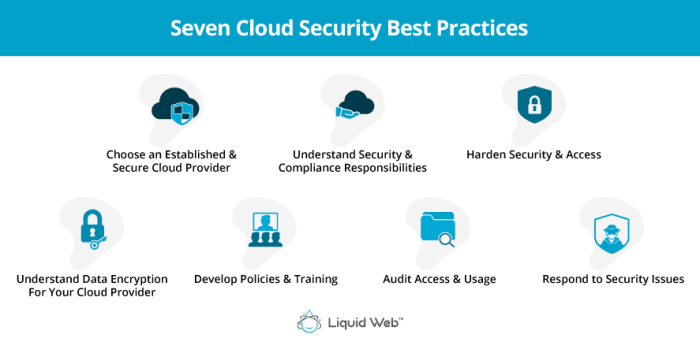
In the dynamic landscape of cloud-based applications, security monitoring and incident response are paramount for maintaining the integrity and resilience of your systems. Proactive monitoring and well-defined incident response strategies are essential for detecting threats, mitigating vulnerabilities, and ensuring business continuity.
Keeping your cloud apps safe is like building a sturdy bamboo hut in Bali – gotta have strong foundations! That means nailing down your security practices, like multi-factor authentication and regular updates. But what about those super-heavy video edits? You’ll need some serious horsepower for that, which is why a dedicated server like the ones mentioned in this article about dedicated servers for video editing might be your best bet.
Once you’ve got that beast of a server, remember to keep it secure too – just like your Bali hut, you don’t want any unwanted guests crashing the party!
Continuous Security Monitoring
Continuous security monitoring is a critical aspect of safeguarding cloud-based applications. It involves the ongoing collection, analysis, and interpretation of security data to identify potential threats, vulnerabilities, and suspicious activities. This process helps organizations stay ahead of security threats, detect anomalies, and respond promptly to incidents.
- Real-time threat detection:Continuous monitoring allows organizations to detect threats in real-time, reducing the time it takes to respond to incidents and minimizing potential damage.
- Proactive vulnerability identification:By analyzing security data, organizations can identify vulnerabilities in their systems before they are exploited by attackers.
- Improved security posture:Continuous monitoring helps organizations understand their security posture, identify areas for improvement, and implement appropriate security controls.
Security Information and Event Management (SIEM)
Security Information and Event Management (SIEM) tools play a crucial role in security monitoring by aggregating security data from various sources, normalizing it, and providing a centralized platform for analysis and reporting. SIEM solutions are designed to detect and respond to security threats by correlating events, identifying patterns, and generating alerts.
- Centralized security data:SIEM tools collect security data from various sources, including firewalls, intrusion detection systems (IDS), antivirus software, and cloud security platforms.
- Threat detection and analysis:By correlating events and identifying patterns, SIEM tools can detect suspicious activities, potential threats, and security breaches.
- Incident response automation:Some SIEM solutions offer automated incident response capabilities, such as triggering security alerts, blocking malicious traffic, and isolating compromised systems.
Incident Response Plan
A comprehensive incident response plan is essential for effectively handling security incidents. It Artikels the steps to be taken in the event of a security breach, including identification, containment, eradication, recovery, and post-incident analysis.
- Define roles and responsibilities:Clearly define the roles and responsibilities of individuals involved in incident response, such as security analysts, system administrators, and legal counsel.
- Establish communication channels:Establish clear communication channels for internal and external stakeholders, including incident reporting, updates, and notifications.
- Develop incident response procedures:Artikel the steps to be taken in response to different types of incidents, such as data breaches, malware infections, and denial-of-service attacks.
- Conduct regular testing and drills:Regularly test and refine the incident response plan through simulations and drills to ensure its effectiveness.
Cloud Security Tools and Services
Securing cloud-based applications requires a comprehensive approach that incorporates various tools and services. These tools and services help organizations manage security risks, monitor their cloud environment, and respond to potential threats effectively.
Comparison of Cloud Security Solutions
Different cloud security solutions cater to specific needs and offer varying levels of functionality. Understanding the strengths and weaknesses of each solution is crucial for selecting the right fit for an organization’s requirements.
- Cloud Security Posture Management (CSPM) Tools:CSPM tools continuously assess the security posture of cloud environments, identifying misconfigurations, vulnerabilities, and compliance violations. They help organizations maintain a secure cloud infrastructure by providing actionable insights and remediation recommendations.
- Cloud Workload Protection Platforms (CWPPs):CWPPs offer a comprehensive approach to securing workloads running in the cloud. They provide features like runtime threat detection, vulnerability management, and data loss prevention to protect applications and data from various threats.
- Cloud Access Security Brokers (CASBs):CASBs act as a security layer between users and cloud applications, enforcing security policies and controlling access to sensitive data. They provide features like data loss prevention, threat detection, and compliance monitoring.
- Cloud Security Information and Event Management (SIEM) Solutions:Cloud SIEM solutions aggregate and analyze security logs from various cloud services, providing a centralized view of security events and potential threats. They enable organizations to detect anomalies, investigate security incidents, and respond effectively.
Cloud Security Posture Management (CSPM) Tools
CSPM tools are essential for maintaining a secure cloud environment by providing continuous monitoring and assessment of security posture. They help organizations identify and remediate vulnerabilities, misconfigurations, and compliance violations.
Keeping your cloud-based apps safe is like building a bamboo hut in the jungle – you gotta be smart about it! Strong passwords, regular updates, and two-factor authentication are your trusty weapons. But if you’re running your own dedicated server, you need extra protection, like a strong, sturdy fence.
Check out How to secure a dedicated server from hackers and malware for some tips. Once you’ve got your server locked down, you can focus on keeping your cloud apps running smoothly, just like the waves on Kuta Beach.
- Continuous Monitoring:CSPM tools continuously monitor cloud environments for security risks, including misconfigured resources, open ports, and unauthorized access.
- Vulnerability Assessment:They scan cloud resources for known vulnerabilities and provide remediation recommendations.
- Compliance Monitoring:CSPM tools ensure compliance with industry regulations and security standards, such as HIPAA, PCI DSS, and GDPR.
- Security Posture Reporting:They provide comprehensive reports on the security posture of cloud environments, highlighting areas of concern and recommending improvements.
Examples of Cloud Security Services
Major cloud providers like AWS, Azure, and Google Cloud offer a wide range of security services to help organizations secure their cloud environments.
- AWS:Amazon offers services like Amazon GuardDuty for threat detection, AWS Inspector for vulnerability assessment, and AWS Key Management Service (KMS) for encryption.
- Azure:Microsoft Azure provides services like Azure Security Center for threat detection and vulnerability management, Azure Sentinel for security information and event management, and Azure Key Vault for encryption.
- Google Cloud:Google Cloud offers services like Cloud Security Command Center for threat detection and vulnerability management, Cloud Armor for DDoS protection, and Cloud Key Management Service (KMS) for encryption.
Security Considerations for Specific Cloud Platforms
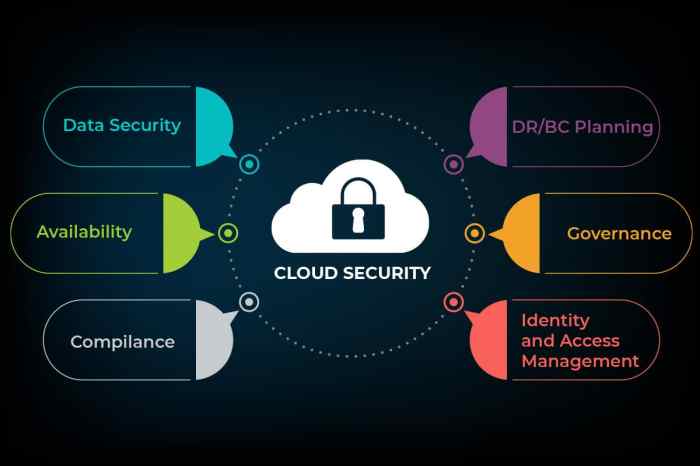
Choosing the right cloud platform is crucial for building secure applications. Each platform offers a unique set of security features and considerations, requiring careful evaluation and implementation of best practices. Understanding these platform-specific security aspects is essential for mitigating risks and ensuring the integrity of your applications.
AWS Security Best Practices
AWS provides a comprehensive suite of security services and features. Here are some key best practices to consider:
- IAM (Identity and Access Management):Implement strong IAM policies to control access to AWS resources. Use least privilege principle and multi-factor authentication (MFA) to enhance security.
- Security Groups and Network ACLs:Configure security groups and network ACLs to restrict inbound and outbound traffic to your instances. Use specific rules based on IP addresses, ports, and protocols.
- Encryption:Encrypt data at rest using AWS Key Management Service (KMS) and in transit using TLS/SSL. Implement encryption for storage services like S3 and databases.
- Vulnerability Management:Regularly scan your AWS resources for vulnerabilities using services like Amazon Inspector and AWS Security Hub. Patch systems promptly to address vulnerabilities.
- Logging and Monitoring:Enable comprehensive logging for all AWS services, including CloudTrail, CloudWatch, and VPC Flow Logs. Monitor logs for suspicious activity and anomalies.
Azure Security Best Practices
Azure offers a robust security framework with features tailored for cloud security. Here are some key best practices:
- Azure Active Directory (Azure AD):Use Azure AD for identity and access management, enabling centralized control over user accounts and permissions. Implement conditional access policies to enforce MFA and other security controls.
- Azure Security Center:Leverage Azure Security Center for vulnerability assessments, threat detection, and security recommendations. Configure security policies and alerts based on your specific requirements.
- Azure Key Vault:Store and manage cryptographic keys securely using Azure Key Vault. Use it for encryption, key rotation, and access control.
- Azure Firewall:Implement Azure Firewall for network security, providing centralized control over inbound and outbound traffic. Configure firewall rules to enforce security policies.
- Azure Monitor:Monitor Azure resources for performance, availability, and security events. Use Azure Monitor to collect logs, create dashboards, and set up alerts.
Google Cloud Platform Security Best Practices
Google Cloud Platform (GCP) offers a comprehensive security model with a focus on data protection and compliance. Here are some key best practices:
- Identity and Access Management (IAM):Use GCP IAM to control access to your resources, implementing least privilege principle and MFA. Define roles and permissions based on specific needs.
- Cloud Armor:Implement Cloud Armor for web application firewall (WAF) protection, mitigating common web attacks and enforcing security policies.
- Cloud Key Management Service (KMS):Use Cloud KMS for managing encryption keys, enabling secure data encryption at rest and in transit.
- Cloud Security Command Center (CSC):Utilize CSC for centralized security management, providing visibility into security posture, vulnerability assessments, and incident response.
- Cloud Logging and Monitoring:Enable comprehensive logging for all GCP services, including Cloud Audit Logs and Cloud Monitoring. Monitor logs for security events and suspicious activity.
Secure Development Practices
In the realm of cloud-based applications, security is paramount. Secure development practices are essential to mitigate vulnerabilities and protect sensitive data. These practices involve incorporating security considerations throughout the entire software development lifecycle (SDLC), from design to deployment.
Security by Design Principles
Security by design emphasizes building security into every stage of the development process, rather than adding it as an afterthought. This approach ensures that security is an integral part of the application’s architecture and functionality.
“Security by design is the practice of incorporating security considerations into every stage of the development lifecycle, from the initial design to deployment and beyond.”
- Identify Security Requirements:Clearly define the security requirements for the application, including confidentiality, integrity, and availability. This helps ensure that the application is designed to meet these requirements.
- Threat Modeling:Conduct threat modeling to identify potential threats and vulnerabilities. This involves analyzing the application’s architecture, data flows, and potential attack vectors.
- Secure Architecture:Design a secure application architecture that minimizes attack surfaces and incorporates security controls such as authentication, authorization, and encryption.
Secure Coding Practices and Vulnerability Testing
Secure coding practices involve writing code that is resistant to security vulnerabilities. Vulnerability testing helps identify and remediate weaknesses in the application’s code.
- Follow Secure Coding Standards:Adhere to established secure coding standards and guidelines, such as OWASP Top 10 and SANS Top 25. These standards provide best practices for preventing common vulnerabilities.
- Use Static Code Analysis Tools:Employ static code analysis tools to automatically scan code for potential vulnerabilities. These tools can identify issues such as SQL injection, cross-site scripting (XSS), and buffer overflows.
- Conduct Dynamic Code Analysis:Perform dynamic code analysis by running the application in a controlled environment and testing its behavior under various scenarios. This helps identify vulnerabilities that are not detected by static analysis.
- Penetration Testing:Engage in penetration testing, where security experts simulate real-world attacks to identify and exploit vulnerabilities in the application. This provides valuable insights into the application’s security posture.
Integrating Security into the Software Development Lifecycle, Server security for cloud-based applications: best practices and considerations
Integrating security into the SDLC ensures that security considerations are addressed throughout the development process, from requirements gathering to deployment.
- Security Requirements Gathering:Involve security experts in the requirements gathering phase to ensure that security considerations are incorporated into the application’s design.
- Security Design and Architecture:Design and architect the application with security in mind, including secure authentication, authorization, and data encryption.
- Secure Development and Testing:Implement secure coding practices and conduct thorough vulnerability testing throughout the development process.
- Security Deployment and Operations:Ensure that the application is deployed and operated in a secure environment, including secure infrastructure, monitoring, and incident response.
Summary: Server Security For Cloud-based Applications: Best Practices And Considerations
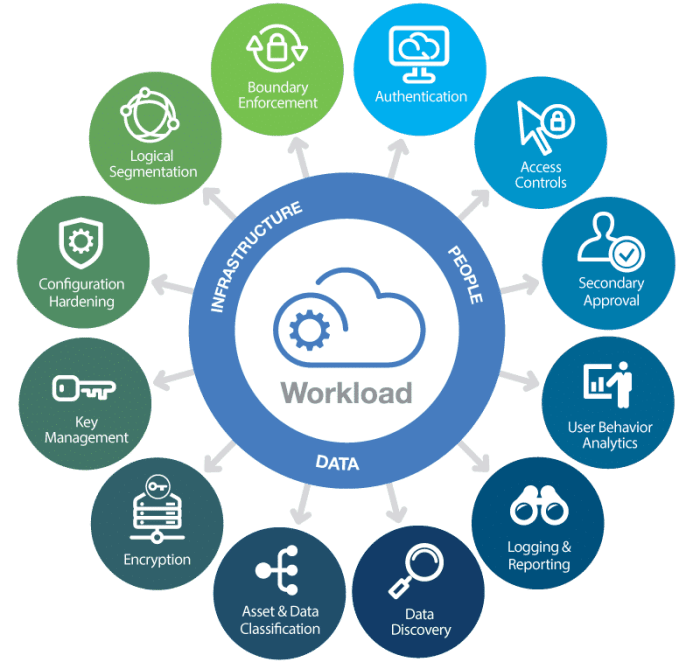
As we conclude this exploration of server security for cloud-based applications, it’s clear that a proactive approach is essential to navigate the complexities of this evolving landscape. By embracing best practices, implementing robust security measures, and fostering a culture of security awareness, organizations can effectively mitigate risks and safeguard their valuable assets in the cloud.
The journey toward secure cloud operations is an ongoing process, demanding continuous vigilance and adaptation to the ever-changing threat landscape.